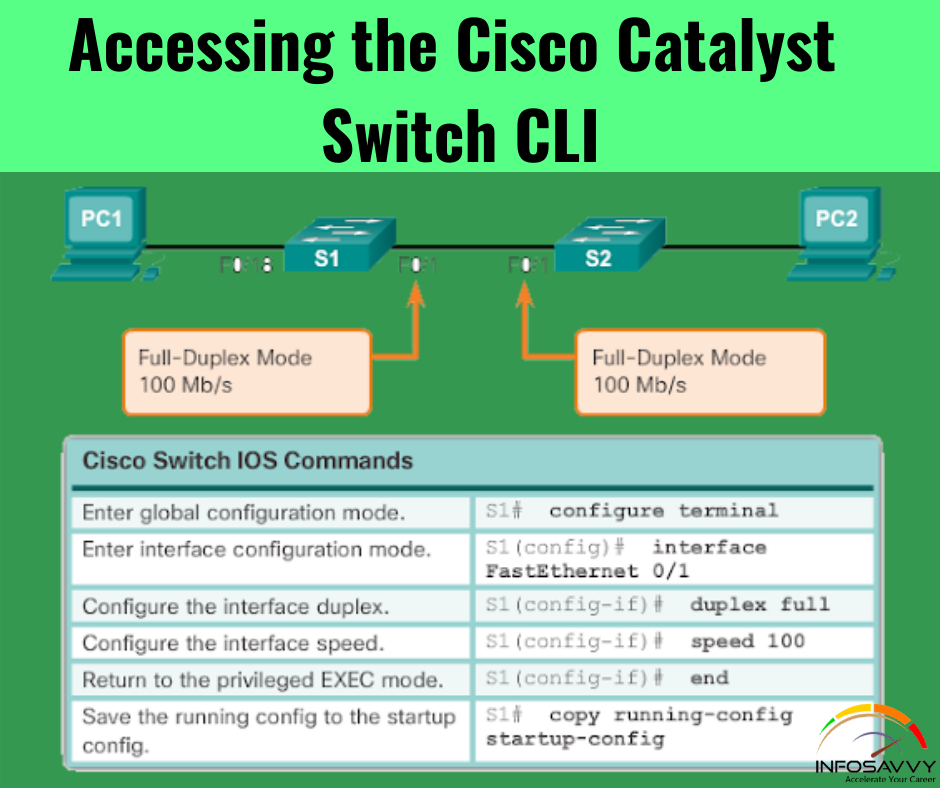
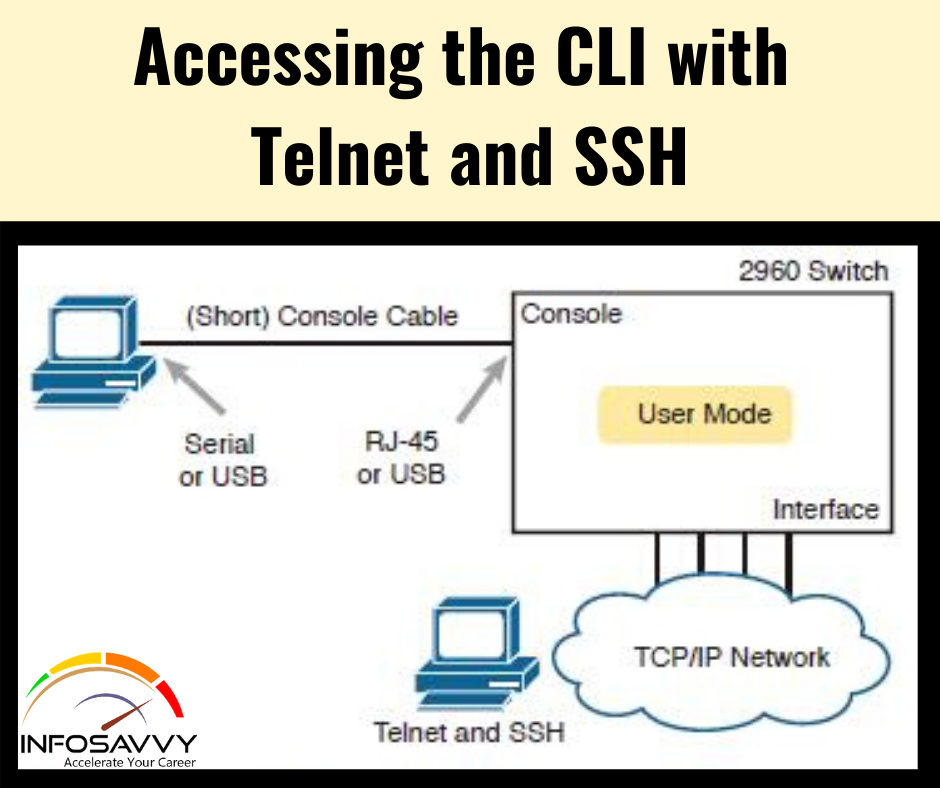
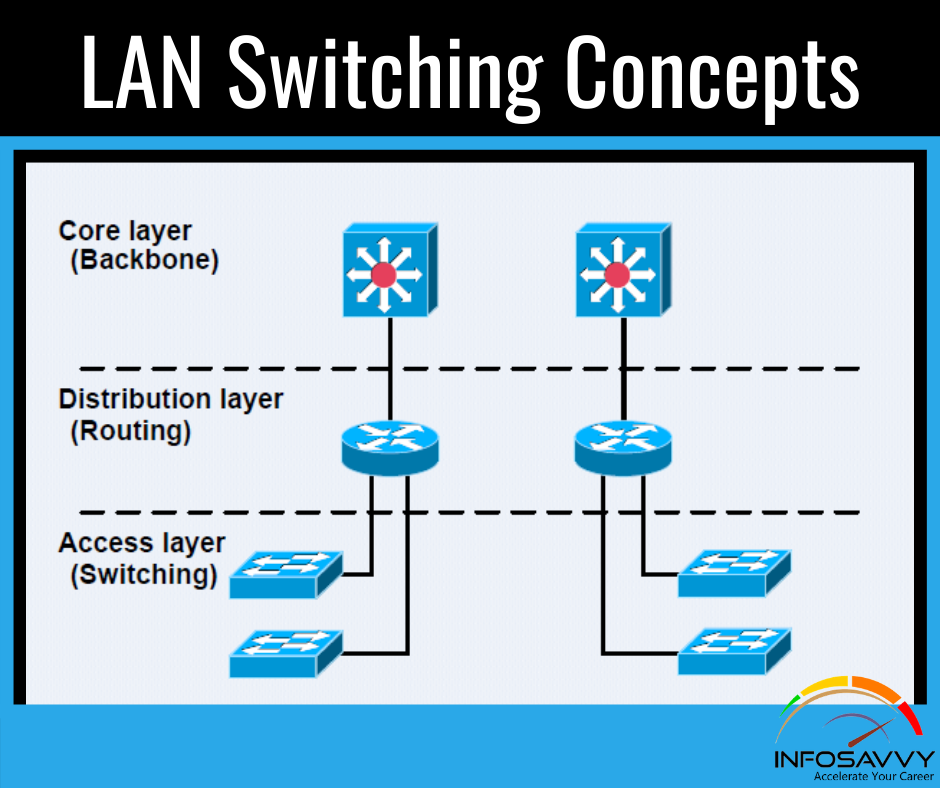
How to Access Cisco Catalyst & Switch CLI
This article is explain How to Access Cisco Catalyst & Switch CLI , Cisco catalyst switches & Accessing the cisco IOS CLI. Cisco uses the concept of a command-line interface (CLI) with its router products and most of its Catalyst LAN switch products. The CLI may be a text-based interface during which the user, typically a network engineer, enters a text command and presses Enter. Pressing Enter sends the command to the switch, which tells …